Secure Your Digital Future with Seepath
At Seepath, we transform security from a cost center into a strategic enabler for growth. Our approach combines Zero Trust principles, AI-driven threat intelligence, and Microsoft’s security ecosystem to protect your apps, data, and networks—while empowering innovation.
Navigate the New Security Landscape
For many businesses, cloud security is a completely new landscape. To guard against modern security threats, traditional security approaches are not enough.
We help organizations build a strong security foundation based on zero-trust security framework with defense-in-depth strategy to defend against threats and mitigate risks.
Elevate your security.
Proactively defend against external threats and insider risks.

Seepath Security Strategy: Unified Protection Across Your Digital Estate
Seepath leverages Microsoft’s most advanced security technologies to deliver end-to-end protection for your organization—across identities, devices, apps, data, and infrastructure. Our approach combines Zero Trust principles with AI-powered threat detection and response.
Azure Sentinel (SIEM + SOAR)
Gain real-time visibility and automated response across your entire digital estate. Aggregate signals from endpoints, identities, apps, and cloud workloads to detect and respond to threats faster.
Identity & PIM
Protect identities with strong authentication and enforce least-privilege access using Privileged Identity Management.
Device Compliance (Intune)
Ensure every device accessing your network is healthy and compliant before granting access.
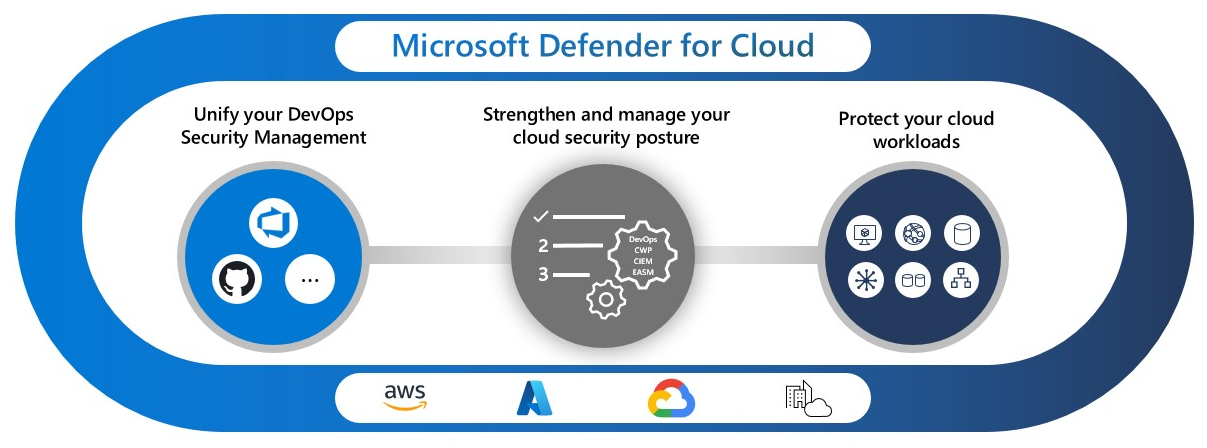
Microsoft Defender for Cloud
Secure hybrid and multi-cloud workloads with advanced threat protection and posture management
Seepath Security Advantage
Seepath provides comprehensive security strategy built on Zero Trust principles. Our unified approach protects your apps, data, and networks across the cloud and on-premises, ensuring resilience against evolving threats.
Enhanced Protection
Seepath Solutions prioritizes your business's cybersecurity. We leverage advanced Microsoft security technologies and best practices to deliver a robust, multi-layered defense against both external and internal cyber threats.
Early Threat Detection
Our real-time threat detection system empowers you to proactively address vulnerabilities, preventing potential breaches before they impact your business.
Rapid Response
Should a security breach occur, our rapid response team will act swiftly. We work closely with Microsoft security experts to minimize impact and ensure rapid recovery.
Seepath Cloud Security Suite
Get a custom security strategy tailored to your unique business needs. Partner with Seepath Solutions to not only protect your assets, but elevate your overall security posture. Contact us today for a free Microsoft-funded security assessment.
Microsoft Defender for Endpoint and Cloud
Next-gen protection for your devices, data and network. Manage your cloud security posture. Prevent, detect and respond to modern threats. Unify DevOps security management.
Vulnarability Management
-
Attack Surface Reduction. Implement secure device configuration policies to resists attacks and exploitation
-
Vulnarability Management. Modern risk-based approach to the remediation of endpoint vulnerabilities and misconfigurations
-
Next-gen protection. Next-generation protection designed to catch all types of emerging threats.
Endpoint Detection and Response
-
Endpoint Detection and Response (EDR). Detect, investigate, and respond to advanced threats.
-
Automated Investigation and Remediation (AIR). Respond to advanced attacks quicly. Reduce the volume of alerts in minutes at scale.
-
Secure Score. Dynamically assess the security state of your enterprise network with actions to improve the security pasture.
Reduce risk by knowing the context
Gain full visibility into your security and compliance posture and understand the most important risks with Defender Cloud Security Posture Management. Get continuous security assessments of your resources across Azure, AWS, Google and on-premises.

Know Your Security Posture
Gain visibility into your organization’s security health and identify gaps before they become risks. Seepath helps you build on your existing investments to protect identities, apps, data, and infrastructure, while enabling your workforce well into the future.
Free Azure Security Assessment
Get a free assessment of your hybrid cloud environment to know where you stand against cyber security threats.
9 Steps to Protecting Cloud Workloads
SEEPATH's two week Azure security implementation gives customers a unique way to optimize, secure and manage their Azure workloads and be compliant.
- Identify security gaps and vulnerabilities
- Assess various attack vectors
- Implement action plan to secure workloads
Your Security Questions—Answered.
Get clarity on your security needs with our expert insights.
Ready to strengthen your security posture?
Schedule your security assessment and discover how Seepath can help you build a resilient, compliant, and future-ready security strategy.